Hello everybody!
Welcome back to the weekly blog post of this serie used to update you with the latest ntopng features and graphical changes. Please let us know your feedback!
Today we are going to talk about the Service Map.
As you probably know, one of the most troublesome problems in a network, when it comes to security threats detection, is discovering Lateral Movements. Lateral Movements can be defined as network activities that an Attacker does when he gain access to a device in the victim’s Local Network, and starts jumping from a local device to an other with the aim of getting access to the device(s) he is really targeting.
In ntopng it is possible to detect those attacks by using the Service Map!
An initial implementation of the Service Map was already available more than one year ago, but we recently improved and optimized this component, both in the backend and the GUI (e.g. by adding more filtering capabilities and improving the user experience when moving between maps and adding filters).
Which information can you find in this map? A lot of useful informations:
- The usual flow tuple (Client, Server, Protocol, Application, Server Port);
note: in case of local connections, the only important thing to detect lateral movement is the server port, the client port is ephemeral. - The number of connections (flows) seen with the same tuple;
- The info field;
These information are really important in understanding and finding Lateral Movements. What is also important is also the ability to set the Learning Period, which is available when configuring the Service Map.
This is used to understand and let the ntopng user decide which flow is allowed in a local network and which not.
It is possible to decide if the flows seen during and after the learning period are: Undecided (let the user check them and put them to Allowed or Denied), Allowed or Denied.
Whenever a flow marked as Denied is seen in the local network, an alert is going to be triggered if the relative check is enabled.
Lastly, we realized that, for large networks, finding a possible lateral movement may be pretty difficult, even with both Service Map representations (map and table). For this reason we decided to add a new view: the Centrality View.
This view is really useful because it gives a rank to the hosts (using an nDPI algorithm that classifies hosts) which helps identifying which hosts are doing suspicious traffic by assigning a high rank to them, other then reporting other interesting information like the total number of Inbound and Outbound edges.
Enjoy!




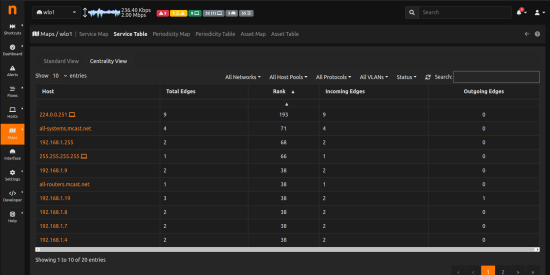






















 With this new table you can immediately see
With this new table you can immediately see 




